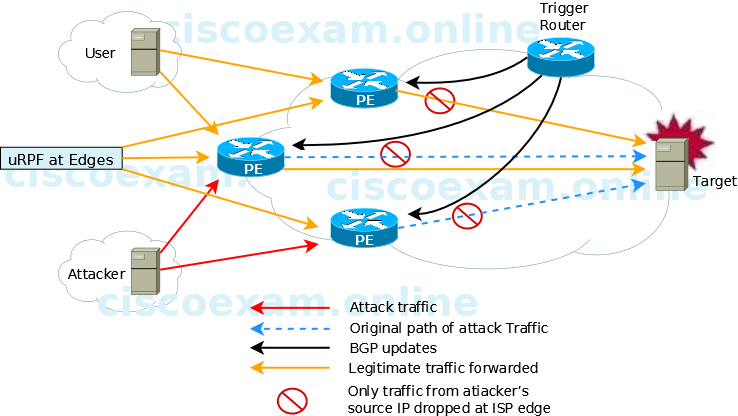
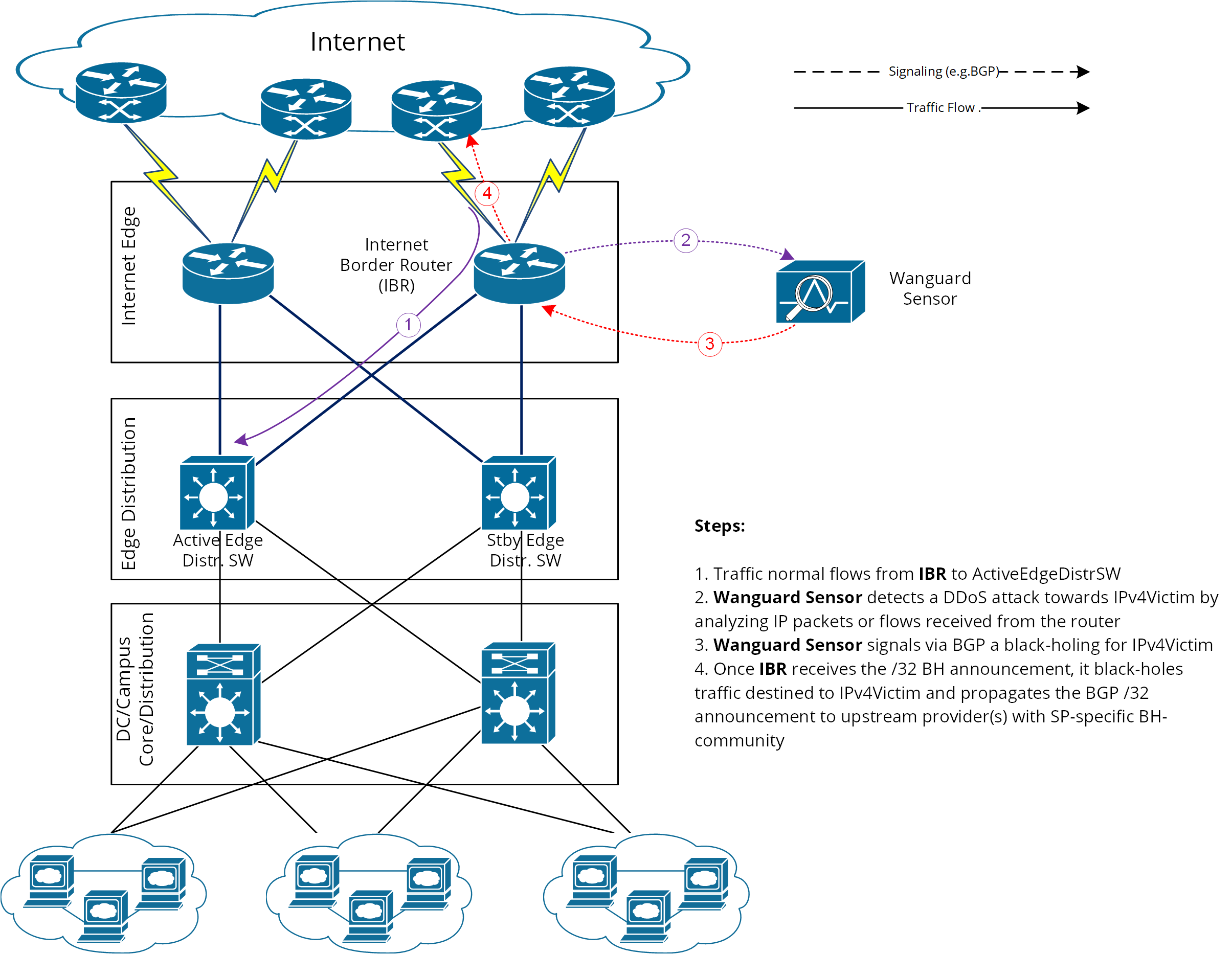
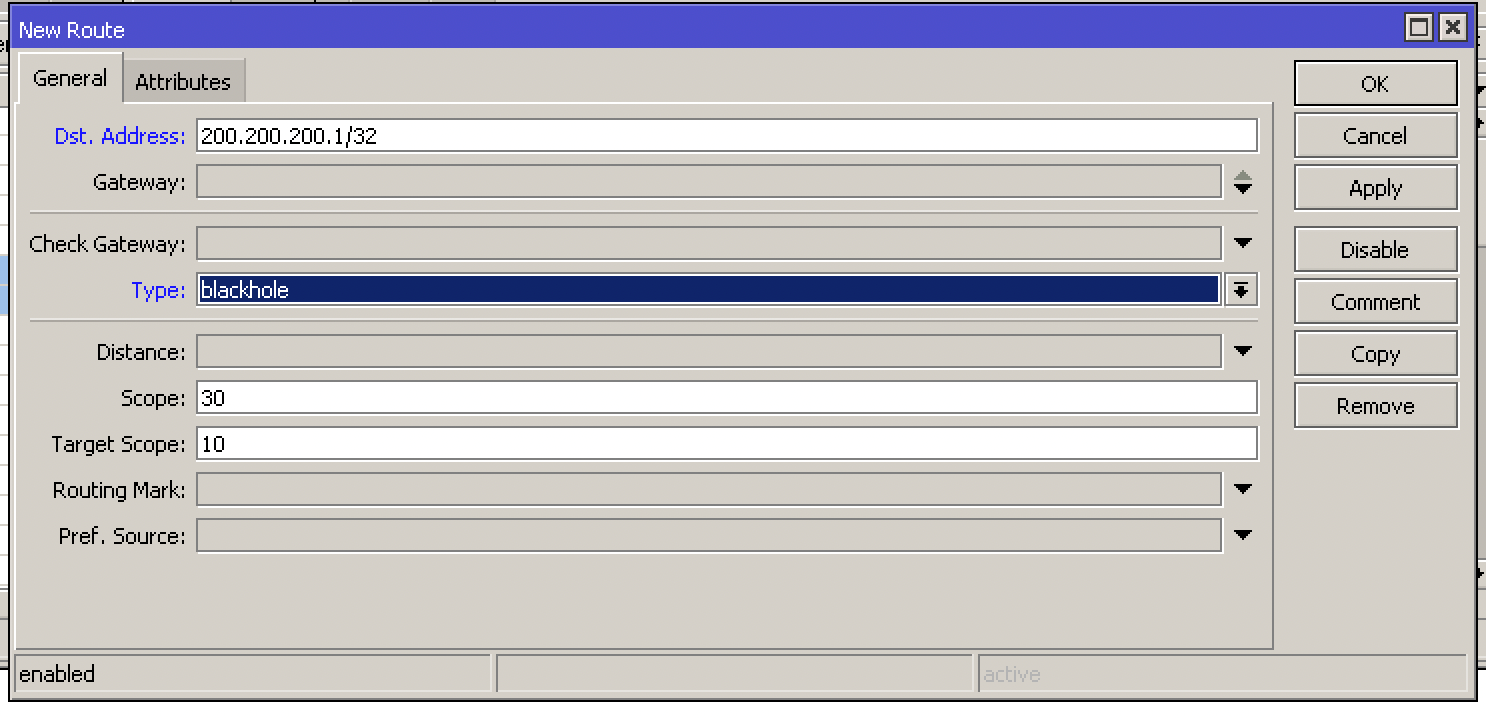
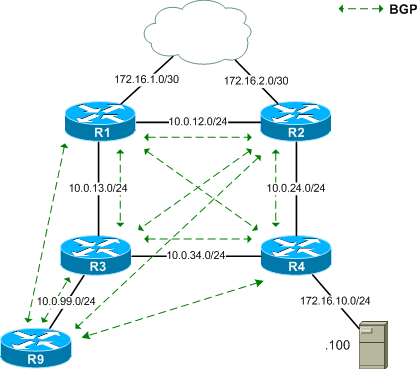
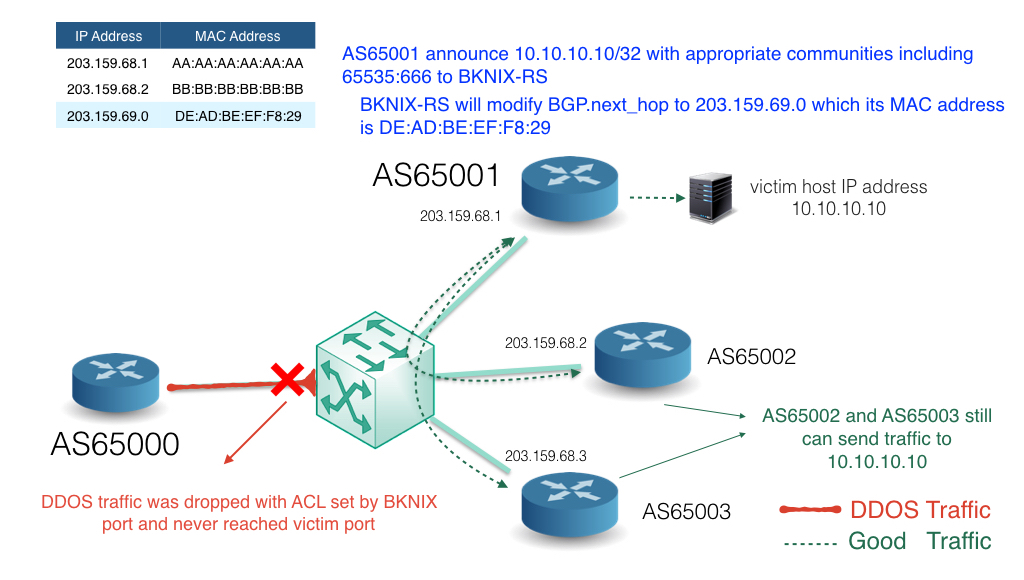
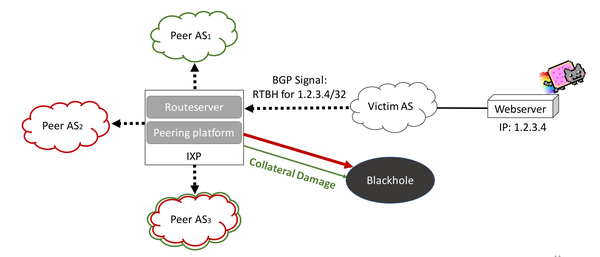
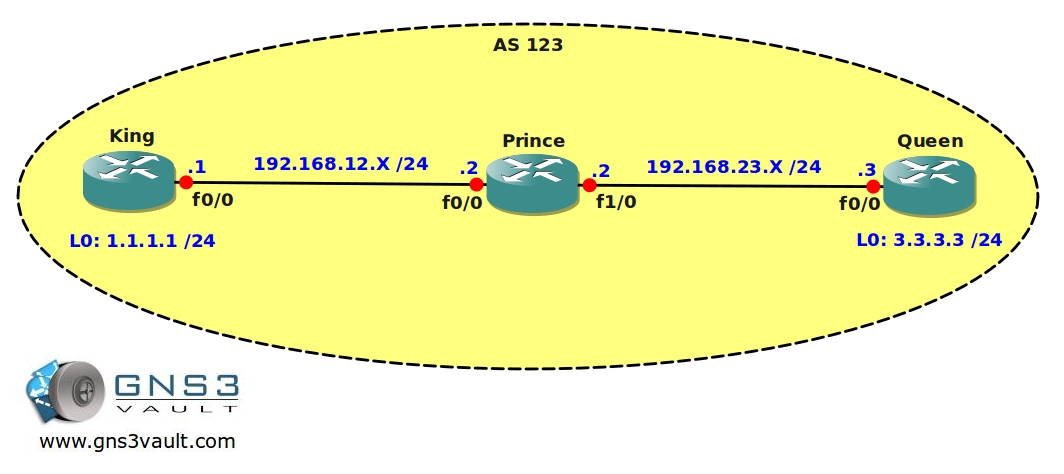
How to configure Remotely Triggered Black Hole routing to protect from DDOS attacks (with bonus) - RouterFreak
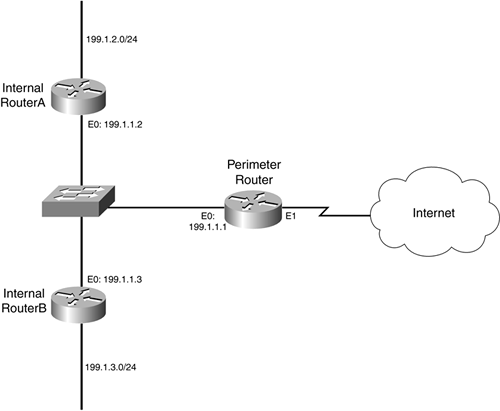
Static and Black Hole Routing :: Chapter 15. Routing Protocol Protection :: Part VI: Managing Access Through Routers :: Router firewall security :: Networking :: eTutorials.org

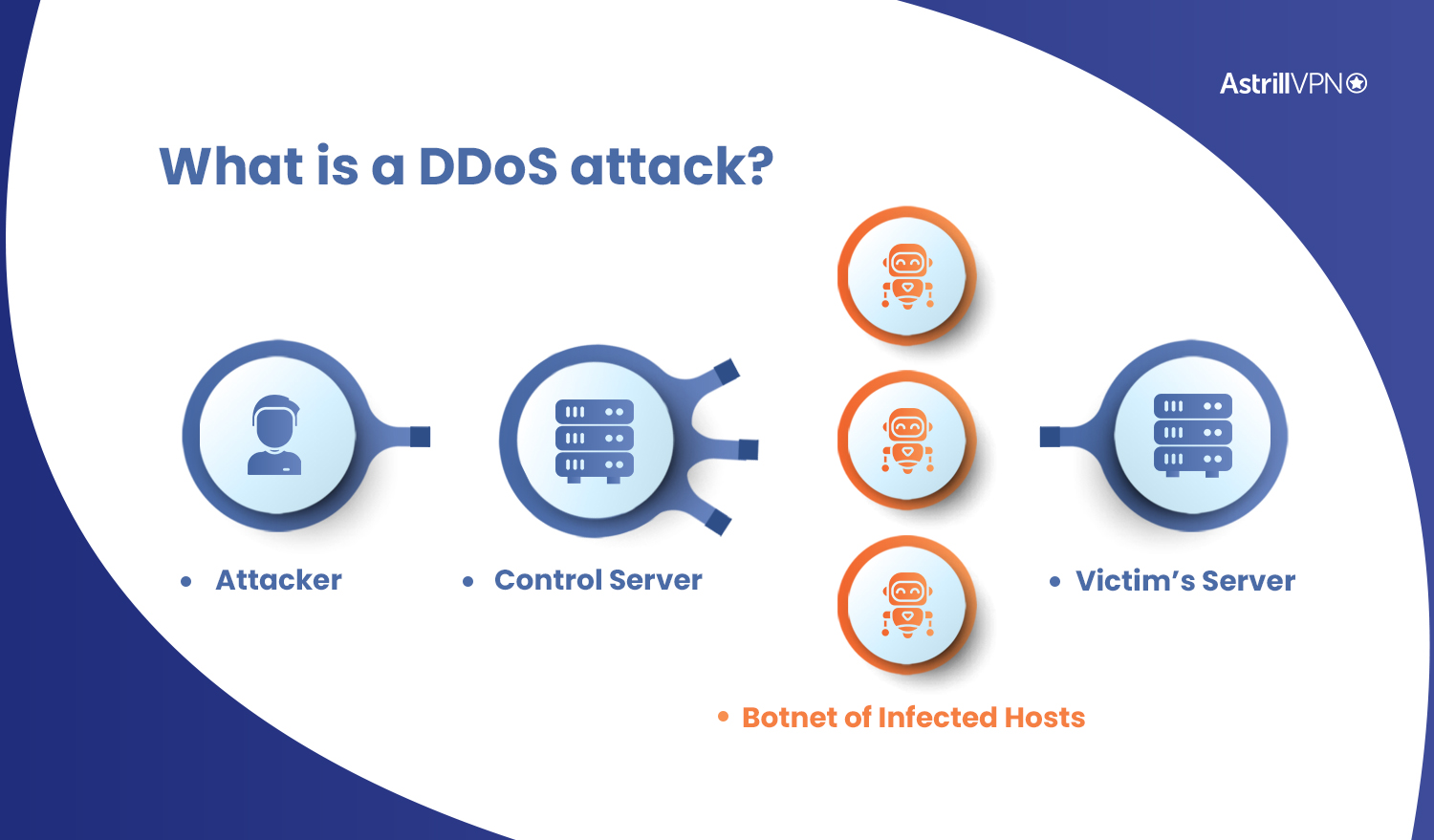
Detecting and analyzing border gateway protocol blackholing activity - Farasat - 2021 - International Journal of Network Management - Wiley Online Library

How to configure Remotely Triggered Black Hole routing to protect from DDOS attacks (with bonus) - RouterFreak